Cordaware bestproxy
The bestproxy security concept
The risks of existing methods:
- High-risk methods: Huge security issues due to port forwarding rules for incoming connections
- Time-consuming deployment processes
- Enormous administration effort causes mistakes
Advantages of the bestproxy security concept:
- Security vulnerabilities will be closed
- No more exception rules for incoming connections
- Deployment processes of services will be sped up drastically
- Zero configuration of the Firewall
The risks of existing methods
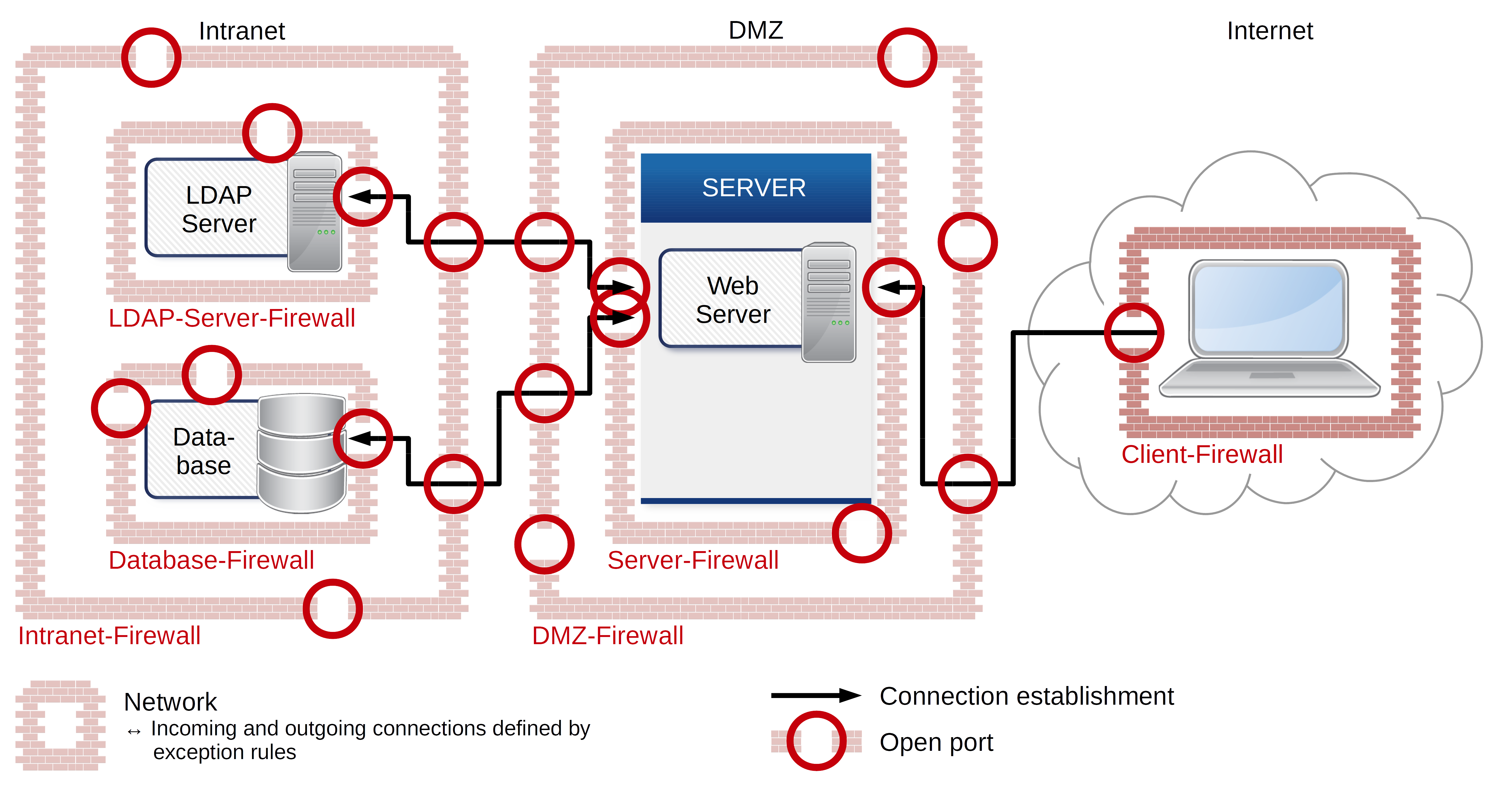
Providing internal data or services by using common solutions creates a high-security issue for your internal network. Defining exception rules for incoming connections for example are very costly, long-lasting and risky methods. Further risks are deployment processes and the administration of ports or even building a complicated DMZ structure. The problem is the numerous amount of exception rules, which become unscreenable very quickly because of their complexity and lead to mistakes. The setup requires an enormous administrational effort every time and your firewalls become vulnerable.
What does the German Federal Office for Information Security say regarding this topic?
“The connection should always be established from the network segment with the higher protection requirement into the network segment with the lower protection requirement.”
“It must be ensured that there is no unauthorized, externally initiated connection set up into the protected network.”
– German Federal Office for Infomation Security
The bestproxy security concept
Cordaware goes new innovative ways! In order to eliminate the problems caused by already existing solutions, we developed the Cordaware bestproxy security concept which is a modern security system.
Replacing complex structures
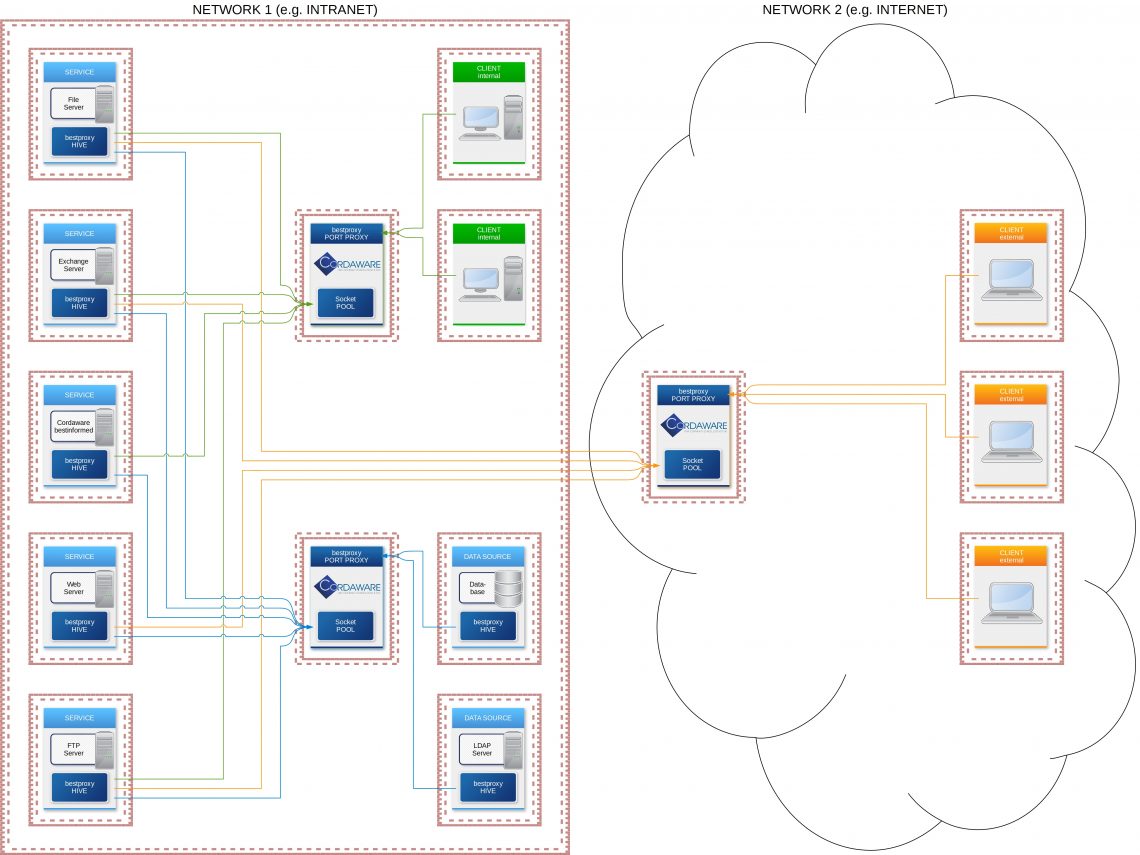
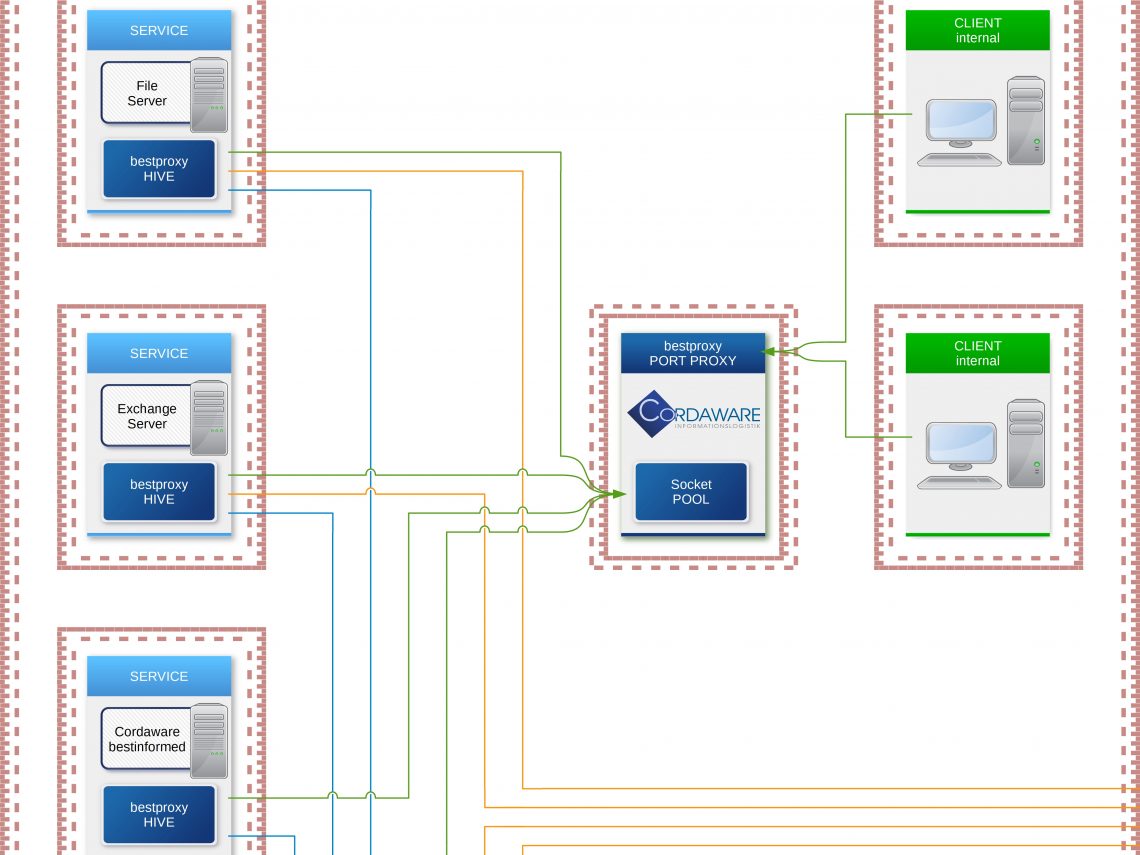
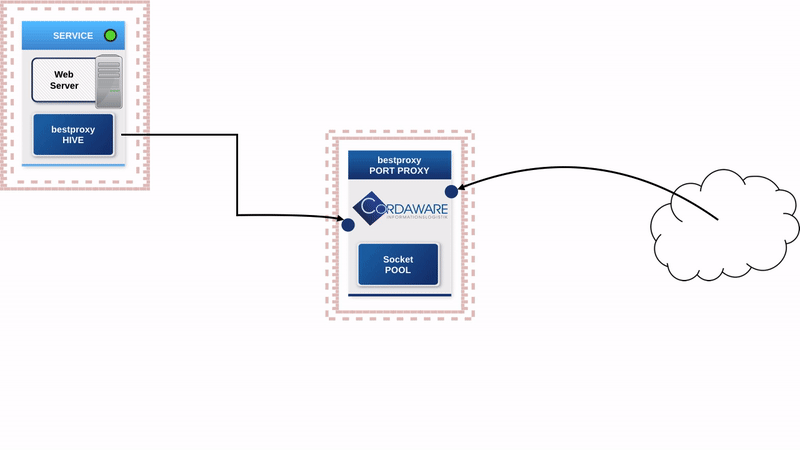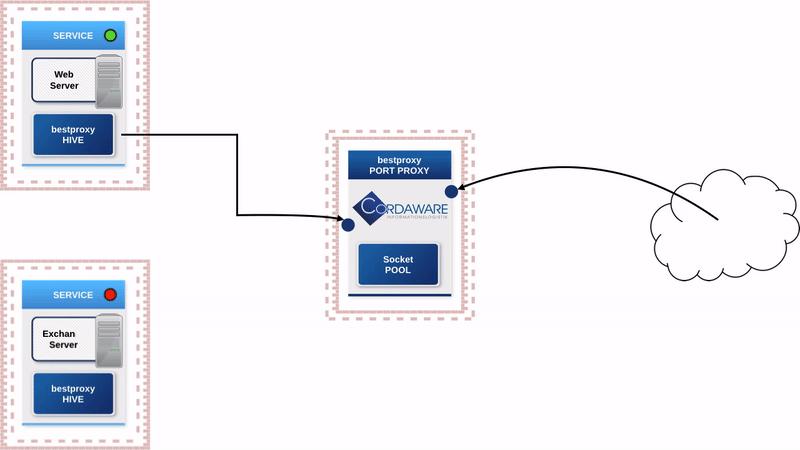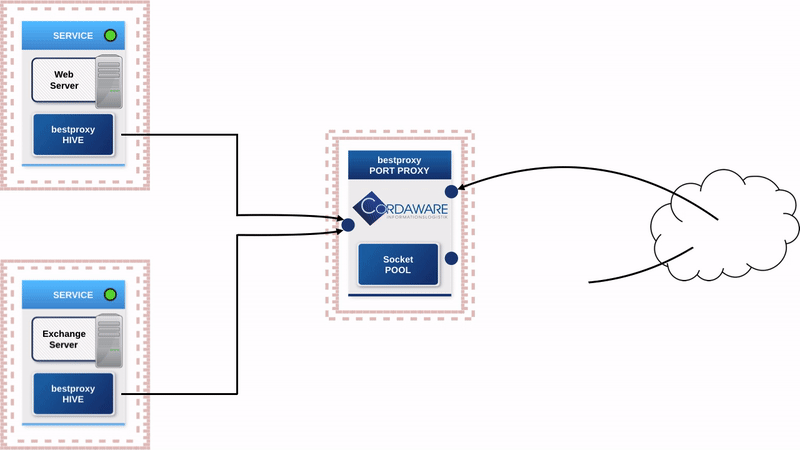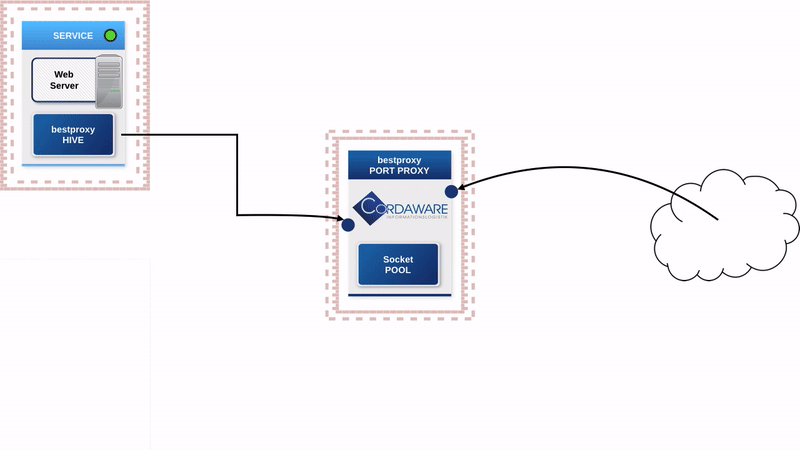
The servers that were located in a DMZ or an in-between network because of accessibility are now moved back into the secured internal network. The so-called "Hive" component of the bestproxy security concept will be installed on these servers.
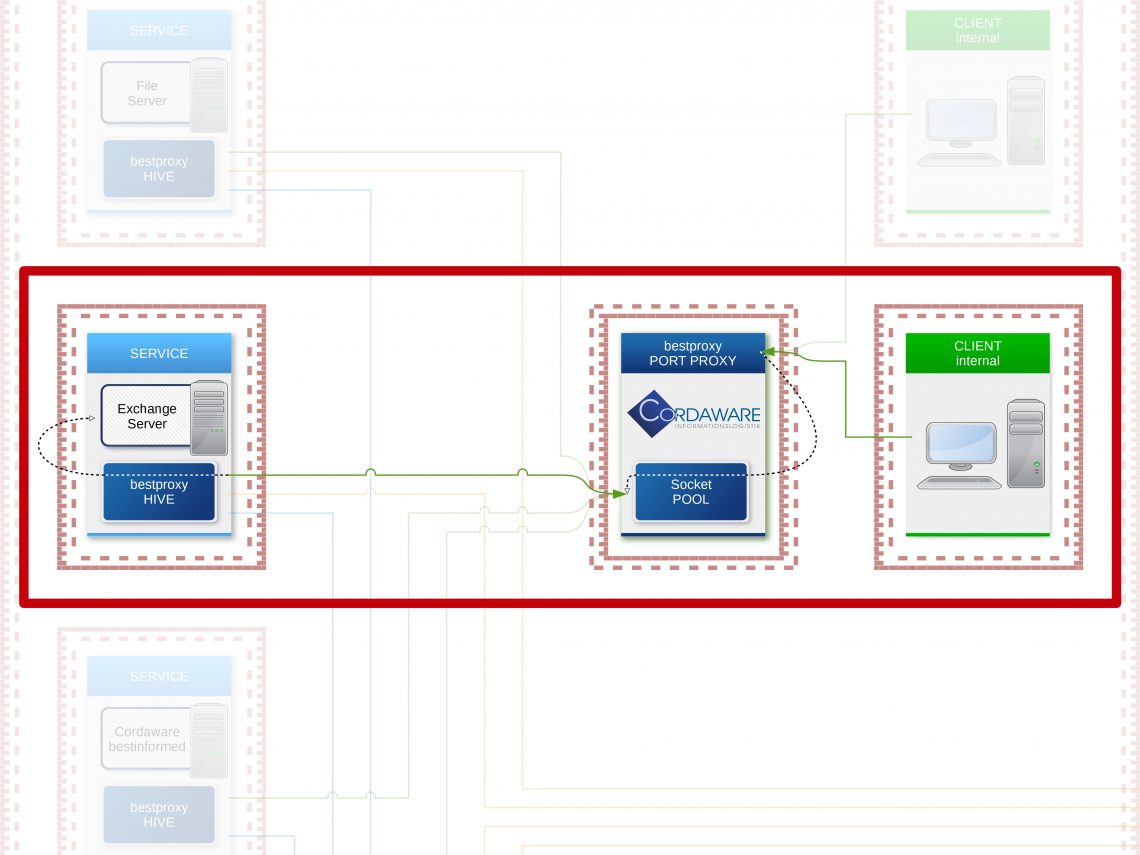
The only component deployed in the in-between network will be the "Portproxy". When a service is started, the "Hive" will automatically establish a connection to the "Portproxy" and supply all configuration details. The "Portproxy" will then open the pre-configured Port of the "Hive" in the outward direction to enable access to the service in the internal network.
Because of this, connections are only established in the outward direction, which means that no exception rules have to be defined in the firewall anymore that enable an incoming connection from the internet or the in-between network into the internal network.
Unified realization
Since not only accesses from external users take place, the basic concept is also transferred to accesses in the internal network. The decisive advantage is that in case of changes or discontinuation of a service, no firewall has to be manually configured and maintained several times, even in the internal network
This results in significant improvements regarding the administrative effort and the clarity of your network infrastructure.
The simplicity of the security concept
The "Hive" automatically establishes connections to the "Portproxy". The "Portproxy" hoards these connections in a so-called "pool". If a user wants to establish a connection to a server, the client first communicates with the proxy. The proxy takes a free connection from the "pool" and communicates with the "Hive" via that connection, which then forwards all data to the actual destination.
Since even the smallest part of your network structure looks like an arbitrarily large part of the overall network, complex untransparent structures are resolved and you always have an overview of your network.
Automate the deployment processes of your services
The bestproxy security concept allows not only to significantly reduce the administration effort of firewalls but also to support the increasing acceleration of provisioning processes through virtualization and automation in IT operations. By integrating the dynamic “Hive” component of the bestproxy concept into your standard containers, you can take the next step of automation. As soon as you start your service, the component automatically establishes a connection to the proxy and tells it which port you have configured for the availability of the service in order to make it available at the same time.
In case of failure or shutdown of the services, it is no longer necessary to close the corresponding port manually. Due to a correlation between service and port, a connection is no longer provided as soon as the service is no longer available. This automation helps you avoid unwanted, unclosed firewall ports and does not consume resources to check or close exceptions.
Overview - The bestproxy security concept
Zero configuration Firewall
So far countless exceptions in the firewall needed to be defined. With the bestproxy security concept, each firewall only needs to be configured once.
In order to realize the source and sink model, incoming connection requests in private networks, as well as outgoing connections from public networks, will be blocked. The Firewalls do not need to be edited after the initial configuration. This way every network structure resembles the other.
Significant shortening of the deployment process for services
In conventional networks, long waiting times arise due to various release instances. These waiting times will be gone with the bestproxy security concept. New services can be deployed via “one-click”.
Huge simplification of the network structure
The manual process of closing and opening ports results in confusing and complex network structures. The management of these network structures can be a high risk and prone for mistakes. The bestproxy automatizes those processes via a correlating management between services and security rules. This way, if a service crashes the associated port will be closed automatically. This way “dead ports” can be avoided and the amount of needed exception rules in the firewall can be reduced to a minimum. This way the risk of wrong configurations is minimized.
No incoming connections from the insecure network to the secured network as recommended by the federal office of information security in germany
In todays infrastructures the deployed services are located in the DMZ and have a bi-directional communication with the databases and LDAP servers which are located in the internal network. These risky structures will be gone due to the bestproxy security concept. The connection will only be uni-directional and the connection will be established from the secure to the insecure network as recommended by the federal office of information security in germany.
Monitoring and notifications
Currently, separate tools are needed in order to monitor services and notify the administrator. These tools are already included in the bestproxy security concept.
Automatized resource on- and offboarding
In order to deploy services, a long chain of processes is usually required. Due to the correlating services and security rules in the bestproxy security concept, these processes will be automatized. If for example a service crashes or gets shut down the correlating port will be closed automatically.
Top facts:
- Zero-Configuration Firewall
- Significant shortening of the deployment process for services
- Huge simplification of the network structure
- No incoming connections from the insecure network to the secured network – as recommended by the federal office of information security in Germany
- Monitoring and notification tools included
- Automatized resource on- and offboarding
- Reduction of risk due to removing complex firewall structures.